How Hostay’s Cleanup Works
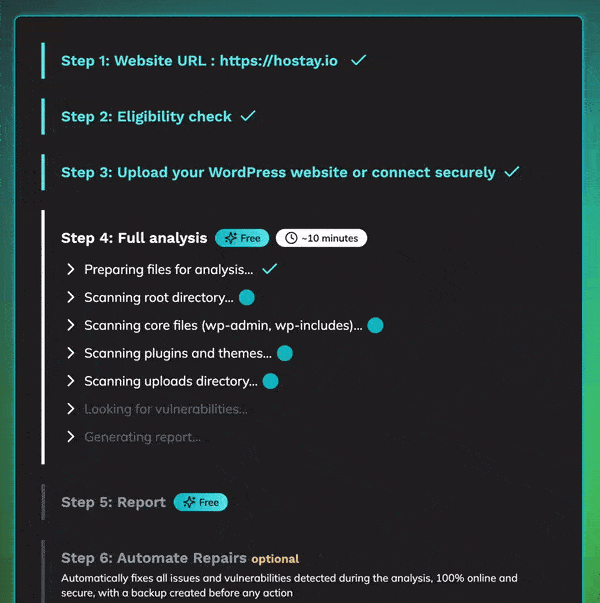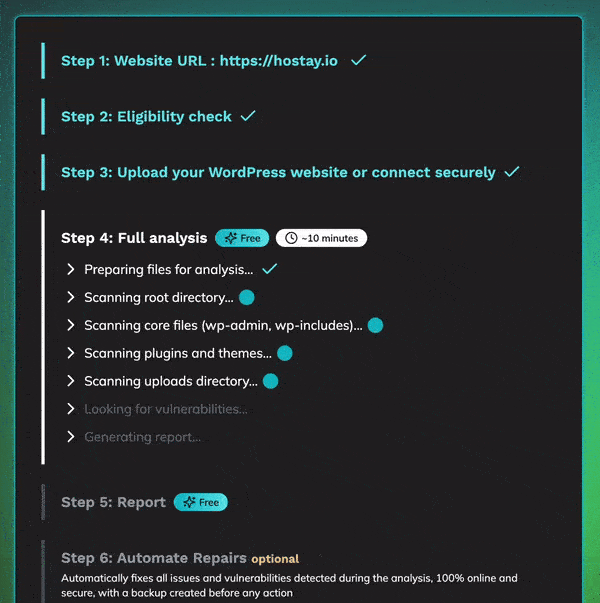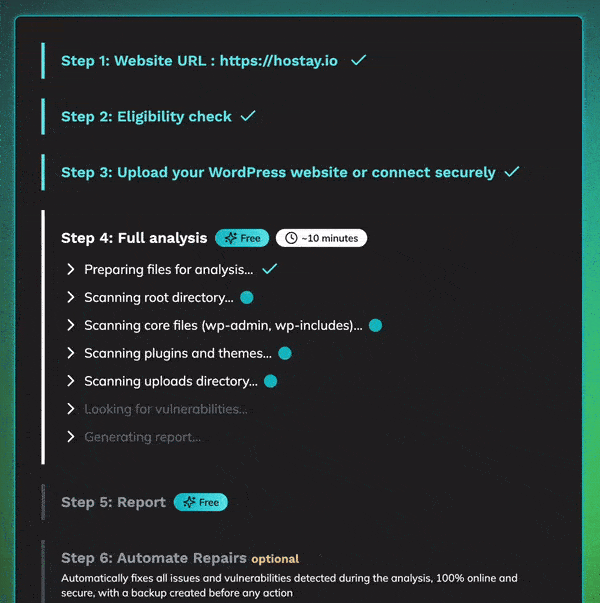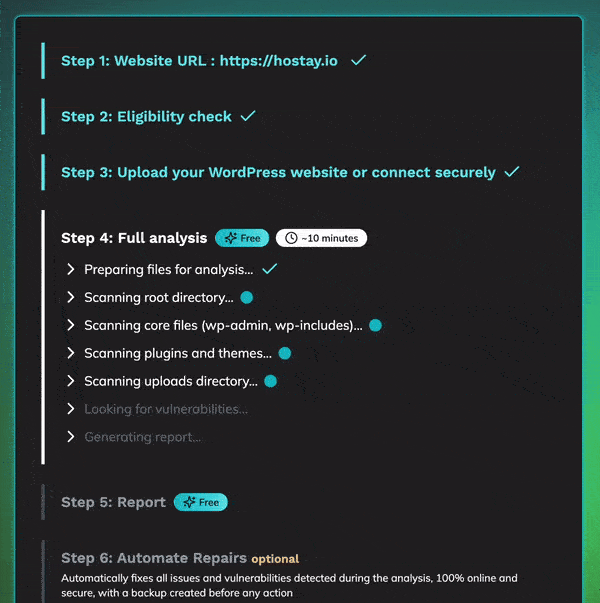
First step : malware and vulnerabilities scan
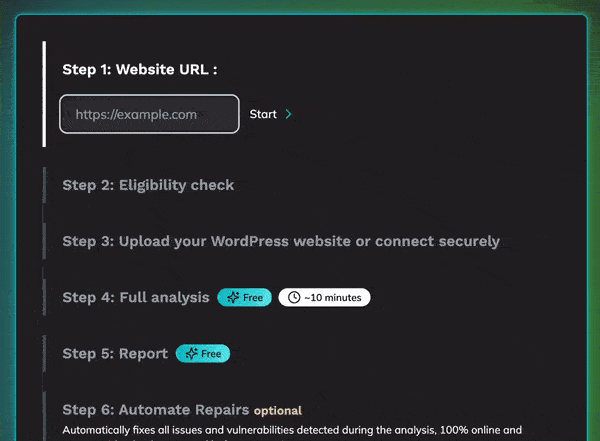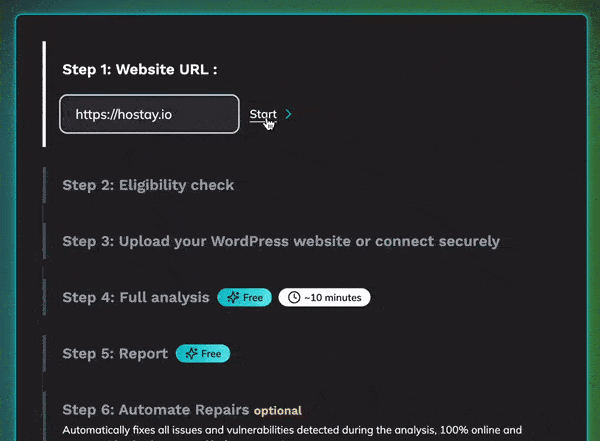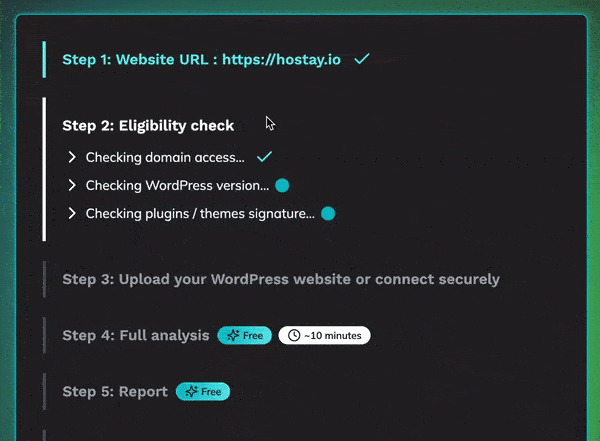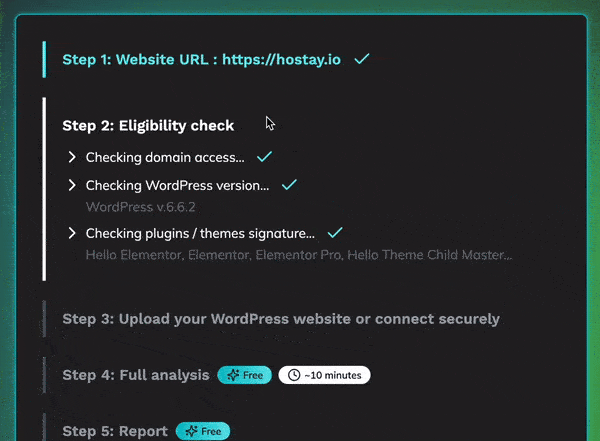
1: Eligibility Check
We first verify that your site is eligible for the scan and cleanup process.
This includes checking:
- Domain status to confirm it’s active and operational.
- WordPress version to ensure compatibility with our tools.
- Installed plugins to identify any potential vulnerabilities or incompatibilities.
2: Provide Data for Analysis
To proceed with a full analysis, choose one of three secure data transfer options:
- ZIP Archive: Upload a ZIP file of your website’s source code.
- All-in-One Migration Export: Use the All-in-One Migration plugin for a safe export.
- SFTP Secure Connection: Allow temporary SFTP access for direct analysis of your site files.
Each option guarantees flexibility and security, making it easy to prepare for the next steps.
3: Full Security and Malware Scan
With your WordPress site data ready, we conduct a comprehensive analysis to detect malware, vulnerabilities, and risks:
- Core file checks for any unauthorized modifications.
- Deep malware detection targeting known and emerging threats.
- Plugin and Theme Integrity Check: We scrutinize the integrity of all installed plugins and themes, comparing them with trusted originals to spot potentially compromised files or security flaws. Any vulnerabilities detected are flagged for immediate attention.
- Known Vulnerability Detection: Leveraging a comprehensive database, we identify vulnerabilities related to your specific setup, pinpointing weaknesses that might have already led to security breaches.
This step provides a complete assessment of your site’s integrity, preparing it for the final cleanup and safeguarding your data against potential threats.
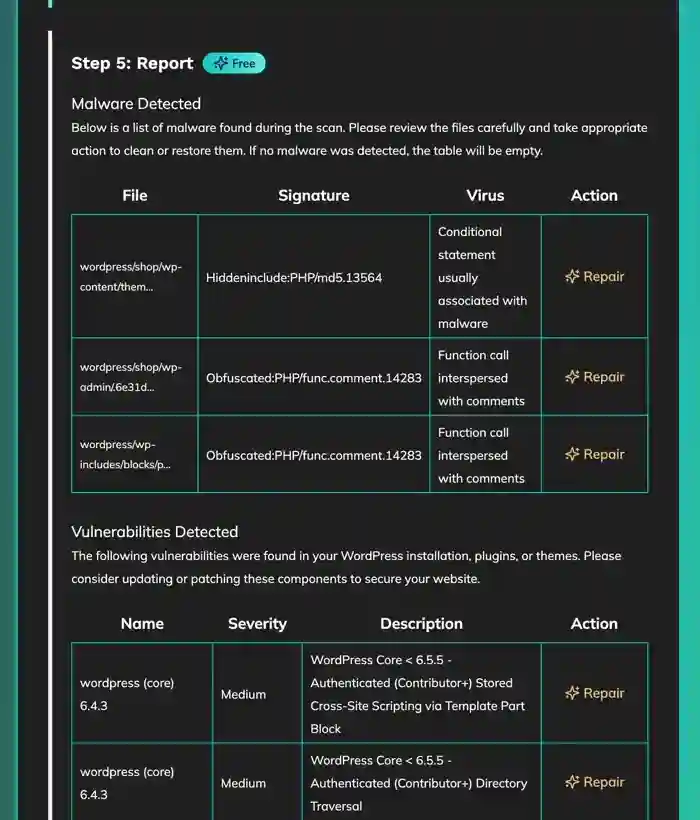
4: Analysis Results
After the in-depth scan, you’ll receive a detailed report that includes:
- Summary of Results: An overview of all detected issues, including malware, vulnerabilities, and flagged files.
- Risk Assessment: Clear labels on each finding, ranked by severity to prioritize action.
This comprehensive report allows you to understand your website’s current state and take informed action to strengthen its protection.
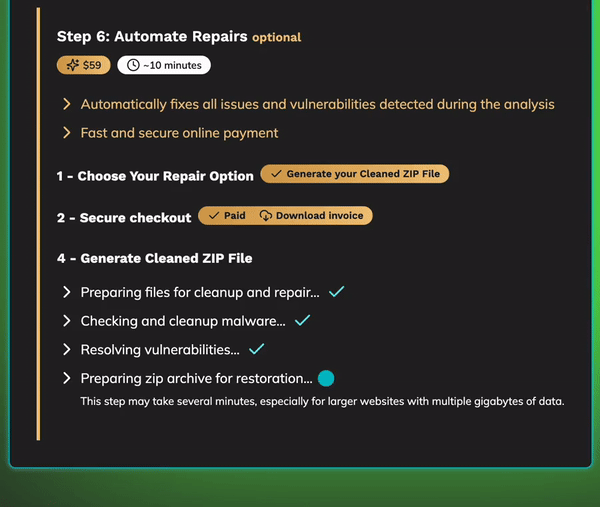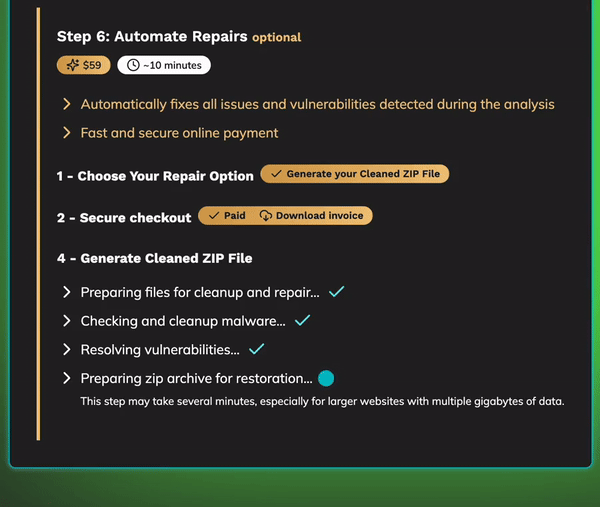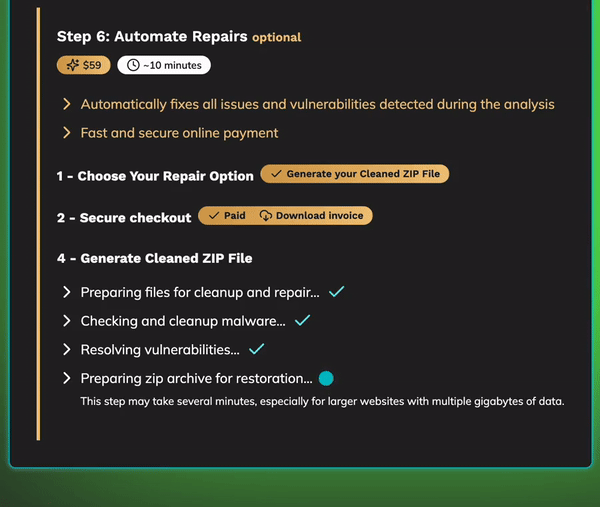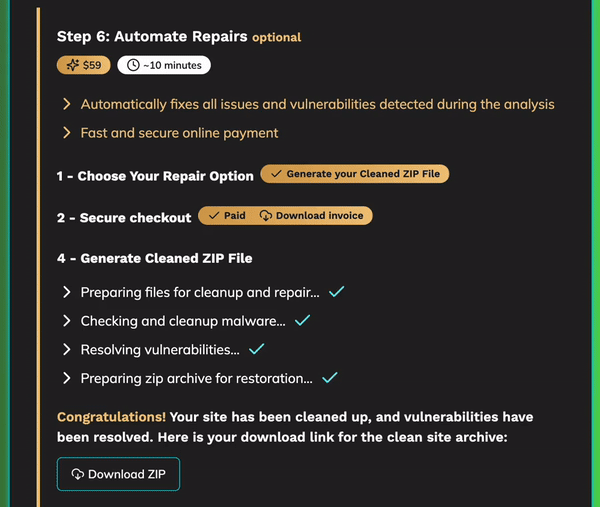
Second Step: Complete Automated Cleanup
Once the scan is completed, our automated cleanup process kicks in, specifically designed to eradicate any malware and patch vulnerabilities quickly and effectively. Here’s a detailed breakdown of what happens:
- Hostay identifies and removes suspicious scripts, backdoors, and unauthorized changes, ensuring the core functionality and data of your site remain intact.
- Vulnerabilities found in plugins, themes, or configurations are quickly patched. Hostay ensures all site components are brought up to secure, updated versions, reducing future risks.
- Throughout the process, you receive real-time updates, giving you insight into each threat that’s being addressed.
- Once the cleanup is complete, Hostay provides a detailed report of all resolved threats, summarizing each action taken for maximum transparency.
Simple, Secure Payment Process
To proceed with a full analysis, choose one of three secure data transfer options:
- Clear and Upfront Pricing Hostay offers transparent, fixed-rate pricing for the entire cleanup service. You’ll know exactly what you’re paying for, with no hidden fees or unexpected charges.
- Payment is securely processed through trusted gateways, Stripe or PayPal, with full encryption to protect your financial information.
- Money-Back Guarantee We stand behind the quality of our service. If you’re not satisfied with the cleanup results, we offer a satisfaction guarantee for the first month. This way, you have complete peace of mind when purchasing.
- Payment confirmation is instant, allowing you to start the cleanup process without delay.
Each option guarantees flexibility and security, making it easy to prepare for the next steps.